Virtual Private Networking (VPN) services, with SSL encryption, offer the internet user an effective way to overcome censorship, surveillance, and access restrictions imposed by oppressive governments or institutions. VPNs in effect provide an encrypted connection between the end user and a distant server which serves as an internet access point. Specifically, the user's IP address appears to be the remote server's location, and any attempts to trace the end user lead to the VPN server. With a typical 128 bit key, data flowing between the user and remote VPN server is encrypted so well that an adversary monitoring the connection will need years of multi-million dollar computing time before the key can be broken by a brute-force attack.
Some VPN users have expressed concern that 128 bit SSL securty is not strong enough, or that their VPN provider does not offer enough flexibility for use of 256 bit SSL gateways. Still others want to use a trusted provider with more layers of encryption to foil surveillance efforts of dictatorial governments, organized crime organizations, or foreign governments with physical access to the VPN servers. One "do it yourself" solution which is effective yet inexpensive is to use multiple VPNs within Virtual Machines. Another solution is to use a "multihop VPN" service.
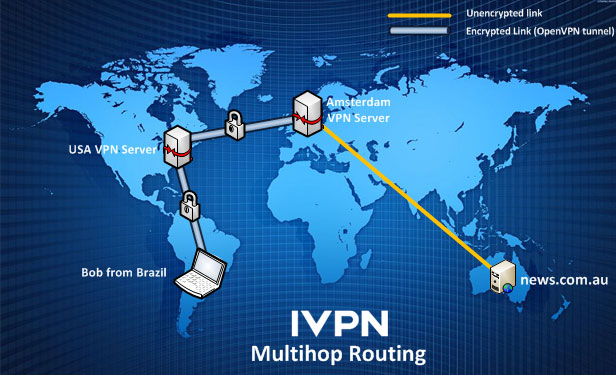
Multihop VPN services are easiest for most persons needing anonymity and security on the internet. All one needs is a single VPN service account and the client software. Connect to a provider's servers and they do all of the multihop routing! Though the user connects to one server, perhaps in the USA, the data exits the VPN at another server, perhaps in the Netherlands. Such services are easy, transparent, and seamless for the end user.
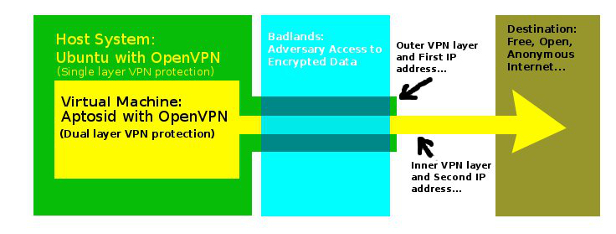
Using a virtual machine for handling sensitive data, with multiple layers of VPN protection.
Multiple VPNs within Virtual Machines means the user of a computer has a VPN service for the main operating system (Linux, Mac, or Windows), and has one or more virtual machines (each with a VPN service) nested within each other as a "box within a box within a box." For example, A journalist may, for example, use a laptop with Ubuntu installed as the main system (using OpenVPN), and use a Virtualbox set up with Aptosid (with its own OpenVPN software). The Ubuntu system can connect to the internet through a free service such as AirVPN while the Aptosid virtual machine uses a Witopia VPN account for security.
How are the VPN layers arranged? Somewhat like an onion - layers inside of layers. The innermost machine has a secure SSL VPN connection that is further encrypted by the main operating system's SSL VPN. The journalist does all of his internet work on the virtual machine with the benefit of two VPNs (one tunnel inside the other) protecting his data and identity. Any number of virtual machines, each with a unique VPN account, can be nested inside one another.As for his IP address, it is the IP address of the VPN gateway on the innermost virtual machine.
Do-it-yourself Multihop VPN Setup:
- Install a VPN service on your computer. OpenVPN works well, and works with popular VPNs such as AirVPN, VPNsteel, and Witopia.
- Install Windows or Linux as a virtualized system. Virtualbox, VMware, or Fusion are popular software packages for this.
- In the virtual machine, install another VPN client.
- Connect each VPN client to different gateways.
In practice, the process of making all of the connections is a bit slow. First, boot the main system. Then start the first virtual machine. If nested virtual machines are used, start each one. After all of the virtual machines are started, go to the main system and connect the outermost VPN layer. Then go to the virtual machine and connect the next deeper layer of VPN protection. For each successive VM, connect its VPN. The innermost layer is the last one to connect, and represents the user's exit point to the outside world.
There are some factors to consider that mitigate the desirability of using nested VPNs to increase security and anonymity on the internet. Using multiple VPNs can be a slow process. The more layers used, the slower will be the connection! For most situations, more than two VPN layers will not be necessary. Services like Hulu and Youtube may work through two VPNs, but will be agonizingly slow through more. VPN connections can be fragile, and three or more nested VPNs may break often enough to interfere with VOIP conversations, downloads, or streaming media. In the final analysis, a trustworthy VPN with 256 bit SSL encryption may be worth the price for all but the most financially distressed internet user.
Don't forget to be meticulous about other areas of communications and data security. Hardware and storage media should be well protected physically in addition to having strong encryption for sensitive data. Likewise, the number people handling sensitive information should be limited. Many a group with high tech encrypted hardware has been compromised by one person's carelessness, followed by the adversary's use of violent interrogation methods. Limiting data access to people with a "need to know" limits the odds of data being given up to interrogators. It is possible for an adversary to detect and interrupt the presence of a VPN connection, and block the ports it uses, but breaking the encryption is nearly impossible.
Recently, the People's Republic of China has set its "Great Firewall" to block VPN traffic using ports 1194 and 443. Witopia and other VPN services were temporarily impaired, but recovered by using other ports and IP addresses. Such is the truth of the fight. Governments that truly serve their citizens have nothing to fear from the free flow of information, while the corrupt, incompetent, or obsolete have everything to fear - and can only delay their ultimate demise with cyber war on VPN services.
Computer users with limited resources can make effective use of modern VPN and virtualization software to build secure and anonymous channels for access to the internet. Surveillance and censorship methods used by repressive governments and institutions can be defeated with nested VPN connections, allowing unfettered two way access anywhere in the world. To a limited degree, governments can interrupt such communication - none have the ability to simply decrypt data sent through a nested VPN tunnel. To use your VPN most effectively, consider these 10 tips for VPN users.
© 2005 - 2024 AB9IL.net, All Rights Reserved.
About Philip Collier / AB9IL, Commentaries and Op-Eds, Contact, Privacy Policy and Affiliate Disclosure, XML Sitemap.
This website is reader-supported. As an Amazon affiliate, I earn from qualifying purchases.