Bootable Linux flashdrives are great tools for portable computing, but one area that has needed improvement is data security. Whomever posesses your USB memory stick, for example, may get access to your personal documents, internet browser (with bookmarks and passwords), email contacts, and all sorts of things that could be harmful in the wrong hands. This page guides you through installation of one, but not the only, method of using strong encryption on your Linux flashdrive.
Not enough time on Earth...
I often use a USB flashdrive which is configured for dual usage: as a bootable Linux device with Firefox, LibreOffice, and other applications, plus an encrypted data folder where I keep important documents, pictures, and other files. The procedure below shows how to use Veracrypt to create an encrypted volume for use by the on-board Linux distro and keep those important files safe. For GNU/Linux, Veracrypt, is available as source code, Debian, and OpenSuSE packages. A brute force attack on this system is quite futile. If all of the computers on Earth were devoted to the attack, the time needed to try all possible keys would exceed the lifetime of the planet. That is the nature of "strong encryption."
Step One - Install Veracrypt
Boot your Linux system, and use your distribution's package manager to retrieve and install Veracrypt:
sudo add-apt-repository ppa:unit193/encryption sudo apt-get update sudo apt-get install veracryptAnother option is to get the latest Veracrypt setup package or source code from the Veracrypt website. If electing to install from source code, be sure to already have the proper kernel headers and "build essential" software installed. Invoke superuser privileges and proceed with compiling and installing Veracrypt. Information below relates to using Veracrypt within Linux Mint and Ubuntu after installing the procompiled module.
Step Two - Create the Encrypted File Container
Open the Veracrypt application. When Veracrypt is running, click the "Create Volume" button to start the Volume Creation Wizard.
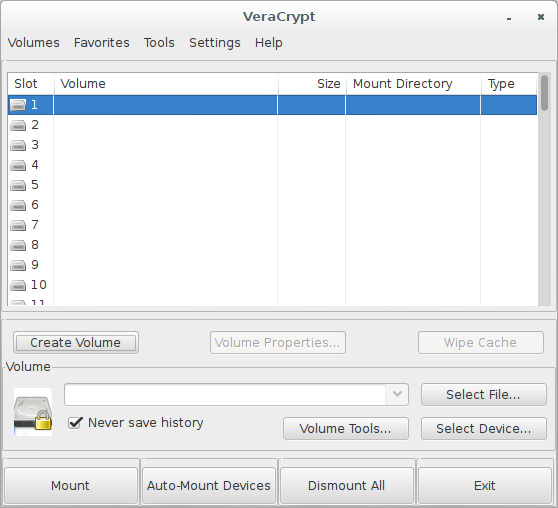
The Volume Creation Wizard will offer two choices of the kinds of available volumes:
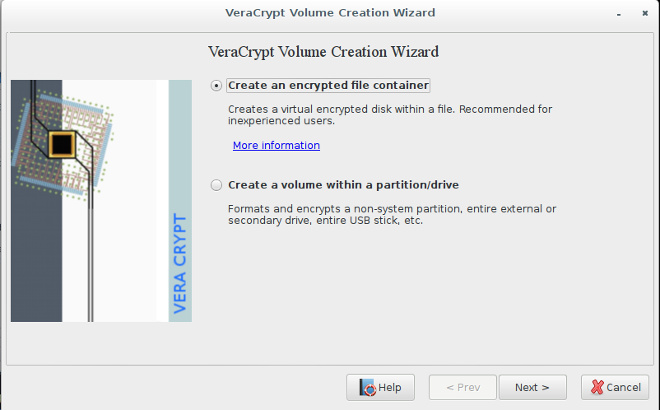
- Creation of an "encrypted file container." This creates one large encrypted archive containing items the user intends to protect from unauthorized access. It uses strong encryption and is orders of magnitude better than password protecting zip and rar archives.
- Creation of an "encrypted volume" within a non-system partition or device. If you have a separate partition on your USB drive for personal data and documents, the whole partition will be protected with this choice. It is used in a similar manner as the file container, but it is a whole partition.
For this article, the choice will be creation of a file container. Follow the menus that pop up and an encrypted container will be created. You should put it within your USB flashdrive (for example, /mnt/sda1/vc0001). The process involves many steps, but you can mostly use the default options. Some choices are rather critical:
- Hidden or standard volumes? A hidden volume can be installed inside a standard encrypted container. Under duress, the user gives up the password for the standard container, and plausibly denies the existence of the hidden volume. Without a correct password, this hidden volume can't be found or proven to exist.
- Use a long password with numbers and both upper and lower case letters. Avoid short words or combinations that can be looked up in a dictionary! Sophisticated adversaries can complete a dictionary lookup attack in minutes. Also, avoid simple number combinations such as birth dates, telephone numbers, etc. The closer your password is to random monkeychatter the stronger it is.
- Making the container too large may cause problems; use no more than 75 percent of the available space.
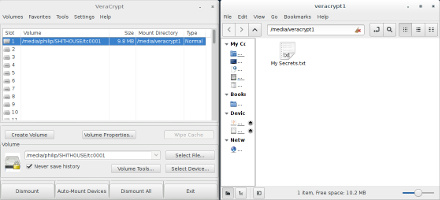
- In the main Veracrypt window, pick a "slot" for your encrypted volume (1, 2, 3, etc).
- Right click the slot, and in the context menu, choose "Select File and Mount..."
- Select and open the encrypted container you have just created (for example, /mnt/sda1/vc0001).
- Another way is to use the "Select File" and "Mount" buttons.
- Enter the proper password when prompted.
Step Three - Move Programs and Data Into The Encrypted Area
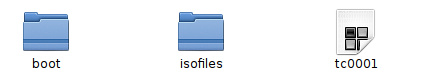
Once the encrypted container has been made, you will have a new file on your USB flashdrive - the encrypted container for your sensitive data. Next you will copy your programs and files to the new container.
Executing the "mount" command opens and decrypts the container, making it available for adding, removing, or even editing files. Operation in the encrypted volume is completely transparent To you, it appears to be just another folder; it is really the decrypted container residing in the system RAM. Operation in the encrypted container is completely transparent. Data encryption is automatically applied to anything inside it.
Simply copy and paste your files into the container, then unmount the container if there are no problems copying the files. Veracrypt closes and protects the container with strong encryption. No-one can get inside now without knowing the password. The data appears quite randomized, and it is resistant to cryptanalysis. You should also delete your original files (now COPIED into the encrypted area), and sanitize the free space outside the container with BleachBit or another secure deletion and free space wiping utility, which will repeatedly overwrite the free space with random data and eliminate traces of previously deleted files.
Procedure Completed!
Bear in mind that the entire USB flashdrive is NOT encrypted. Veracrypt has been installed and an encrypted container has been created on the USB flashdrive. If the USB flashdrive is lost or stolen, the encrypted data can not be accessed. Sleep soundly, without worry about who is reading your USB stick.
© 2005 - 2024 AB9IL.net, All Rights Reserved.
About Philip Collier / AB9IL, Commentaries and Op-Eds, Contact, Privacy Policy and Affiliate Disclosure, XML Sitemap.
This website is reader-supported. As an Amazon affiliate, I earn from qualifying purchases.